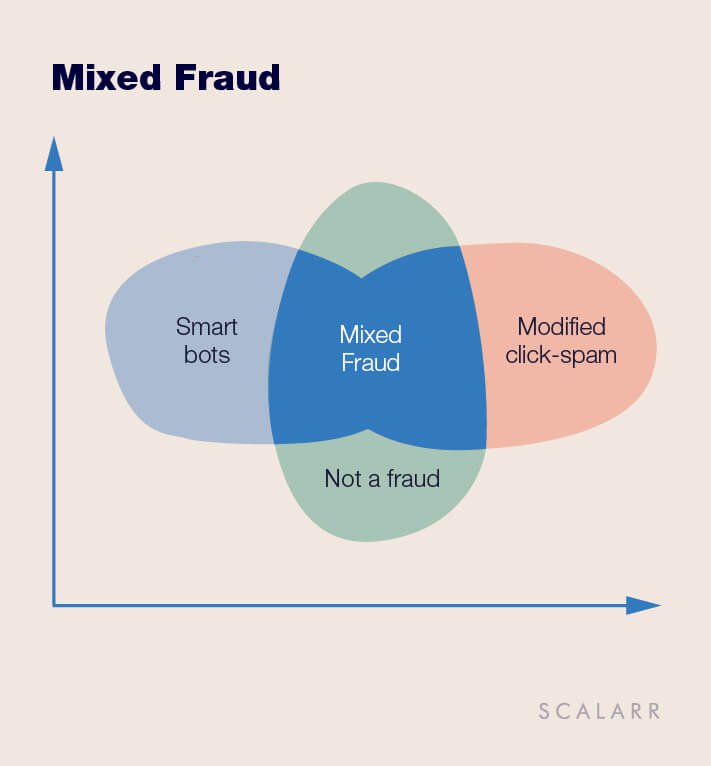
Mixed fraud represents different kinds of fraud mixed in one indivisible bundle. Such a bundle can comprise several types of fraudulent traffic or fraudulent and non-fraudulent traffic mixed together. This type of fraud is related to the New Face of Mobile Fraud category.
Quick Facts
1. Mixed Fraud or "Mixes" were first found in April 2018 in e-commerce apps, combined two types of fraud and real users in one bundle.
2. In 2018 mixed fraud was responsible for 15,3% of all fraud cases.
3. At the moment, the only effective measure to protect against Mixed Fraud is traffic clustering technology.
How Mixed Fraud works
Mixed Fraud is hardly detectable and there are no obvious patterns that could be visually recognized. The mixing options are the following:
- the conscious use of several different types of fraud to overcome known protection measures of anti-fraud services
- a chaotic mixture of different types of fraud in the case of connecting to the publisher with an uncontrolled number of re-brokering levels.
As a result, different types of traffic are mixed in one indivisible bundle, making common anti-fraud metrics and patterns inefficient in this case.
The most widespread types of mixes are the following:
1. Real Paid Users + Classic Bots
In this case, fraudsters try to imitate low performance with the help of bots in order to make it similar to paid traffic. Advanced fraudsters also can emulate in-app purchases (from stolen credit cards or make a minimum possible purchase, starting from $0,1). Usually, this subtype of Mixed Fraud can be disclosed by a suspicious level of paying users (the percentage of such users can be much higher than average) with no repetitive purchases and all events occur in the first 2-5 minutes after install.
It’s also worth taking a look at e-commerce apps and how real users behave: they search for products and then an event “product open” took place. Such events are repeated by real users (usually they perform about 25-30 “product open” events) since they choose an item and review product page before the purchase. If we're dealing with fraudsters, we usually see an insignificant number of “product open” events (usually 2-3 events).
One of the ways to prevent such a subtype of Mixed Fraud is to change the traffic purchase model from CPI/CPA to RevShare - such a model is not profitable for fraudsters.
2. Click Spam + Classic Bots
Fraudsters launch their bots simultaneously with stealing of organic installs through the Click Spam. Such a Mixed Fraud subtype is hard to identify since the indicator “number of users with TTI up to an hour” increases to the level of non-fraudulent traffic, therefore it becomes impossible to define the presence of Click Spam with a high probability. Also, Click Spam means real users who perform events in the app.
3. Click Injection + Real Users
Such subtype of mixes also take place but is much less common than the two previous subtypes.
How to deal with Mixed Fraud
The mobile ad fraud battleground is constantly changing. If fraudsters are caught in one field, they usually move on to a different, newer and more promising patch. So stopping them with your own is a very difficult goal.
The only effective measure of protection against different variations of Mixed Fraud is traffic clustering technologies: when the machine learning algorithm fully isolates individual fraudulent clusters inside the indivisible bundle and clearly recognize fraudulent and non-fraudulent traffic, as well as the various types of fraud within.
Read Scalarr’s Ultimate Guide to Mobile Fraud Types to understand more about dealing with Mixed Fraud in all specific cases.
The only solution for mobile advertisers is to partner with anti-fraud tools that make use of powerful and intelligent technologies such as machine...
The road to Scalarr's foundation was paved with challenges and opportunities and in this in-depth conversation, you'll learn the story of Scalarr f...